Symantec released a great 7 Tip Stratedgy for SME for their IT infrastructure last year and I thought I would share this today, as its still very prevalent.
1. Know what you need to protect
One data breach could mean financial ruin for an SMB. Look at where your information is being stored and used, and protect those areas accordingly.
Note: Maybe consider an Internal Private Cloud System to store all important Data. Pc Clean can offer this Service
2. Enforce strong password policies
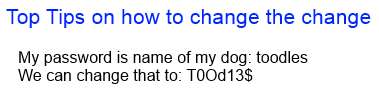
Passwords with eight characters or more and use a combination of letters, numbers, and symbols (for example, # $ % ! ?) will help protect your data.
Note: Change password at least Twice a year for particular websites and never use the same password for more than one site. Pc Clean can provide solutions on how to deal with passwords and what security mechanisms and polices SMB’s need.
3. Map out a disaster preparedness plan
Don’t wait until it’s too late. Identify your critical resources, use appropriate security, and backup solutions to archive important files and test frequently.
Note: What is the point of having Backup’s that won’t work. I have seen too many Offices saying they have Backup Server, only to find out it stopped backing up 2 years ago! Pc Clean can provide solutions on how to monitor Backups and test their validity
4. Encrypt confidential information
Implement encryption technologies on desktops, laptops, and removable media to protect your confidential information from unauthorized access, providing strong security for intellectual property,customer, and partner data.
Note: There are many Free and Paid solutions on the market to encrypt Data. A simple question to ask yourself, “Are you confident all devices have at least a Logon Password that would be strong, as mentioned in Point 2? Pc Clean provide policies and instructions for all the team to better understand the strength of encryption.
5. Use a reliable security solution
Today’s solutions do more than just prevent viruses and spam; they scan files regularly for unusual changes in file size, programs that match known malware, suspicious email attachments, and other warning signs. It’s the most important step to protect your information.
Note: There are many Free and Paid solutions on the market that promise to protect our computers. But we get never opt for 100% protection, but we can get as close to it as possible.
Are you comfortable with the current solution? If not, Pc Clean supplies software from a few of the Top leading vendors. We only sell software, we use on our own systems, that we rely on.
6. Stay up-to-date
A security solution is only as good as the frequency with which it is updated. New viruses, worms, Trojan horses and other malware are born daily, and variations of them can slip by software that is not current.
Note: Many security packages need our input to work to its potential, many us may not know this nor have the time to fuss about with it.
What attention does your security package need? If not, Pc Clean supplies software from a few of the Top leading vendors. We only sell software, we use on our own systems, that we rely on.
7. Educate employees
Develop Internet security guidelines and educate employees about Internet safety, security and the latest threats, as well as what to do if they misplace information or suspect malware on their machine.
Note: We mostly believe the hacking comes from outside the workplace eg. Online. But many times, the staff maybe the weakest link. Make sure staff know the security concerns also.
Michael Boyd, from BoydHr.ie specialises in human resources and how to manage the staff efficiently his is mission. In terms of internal staff issues and how to respond to in-house concerns, contact Michael before the damage is irreversible.
Disclaimer: These 7 Tips are from Symantec’s report in April 2012 and can be found here. Extra notes and information is written by www.CyberSafetyAdvice.com









No comments yet.